Hsinchu, Taiwan – November 18, 2019 – AegisLab reviewed several CVE (https://cve.mitre.org/) entries and found the following 2018 CVE Vulnerabilities are not fixed yet. The CIRCONTROL is notified by the email on Oct 15 but no response so far. AegisLab has done the obligation to report to CIRCONTROL one month before publishing security report. Actually CIRCONTROL should begin fixing these vulnerable devices since 2018 but they did not.
The header of Lionic’s notifying email -
To: circontrol@circontrol.com
From: ???? ????? <????.?????@lionic.com>
Subject: [Security Alert] Several CirControl appliances still have
CVE-2018-16670 vulnerability
Message-ID: <71427573-c84c-8aa5-0710-9f7239e492b7@lionic.com>
Date: Tue, 15 Oct 2019 16:08:23 +0800
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:60.0) Gecko/20100101
Thunderbird/60.9.0
MIME-Version: 1.0
Content-Type: multipart/alternative;
CIRCONTROL is a Spanish company which provides eMobility solutions including EV chargers. They can integrate the EV chargers into the parking space. So that electric vehicle is charged while parking. Their three vulnerabilities are -
-
CVE-2018-16670 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-16670)
An issue was discovered in CIRCONTROL CirCarLife before 4.3. There is PLC status disclosure due to lack of authentication for /html/devstat.html.
-
CVE-2018-16671 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-16671)
An issue was discovered in CIRCONTROL CirCarLife before 4.3. There is system software information disclosure due to lack of authentication for /html/device-id.
-
CVE-2018-16672 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-16672)
An issue was discovered in CIRCONTROL CirCarLife before 4.3. Due to the storage of multiple sensitive information elements in a JSON format at /services/system/setup.json, an authenticated but unprivileged user can exfiltrate critical setup information.
However, CIRCONTROL do not emphasize the safe programming. The CIRCONTROL chargers connected to Internet is easy to be found by the famous Shodan service (https://www.shodan.io/search?query=circarlife).
The following screenshots are captured on Nov 1. You may obtain different result since the time is different.
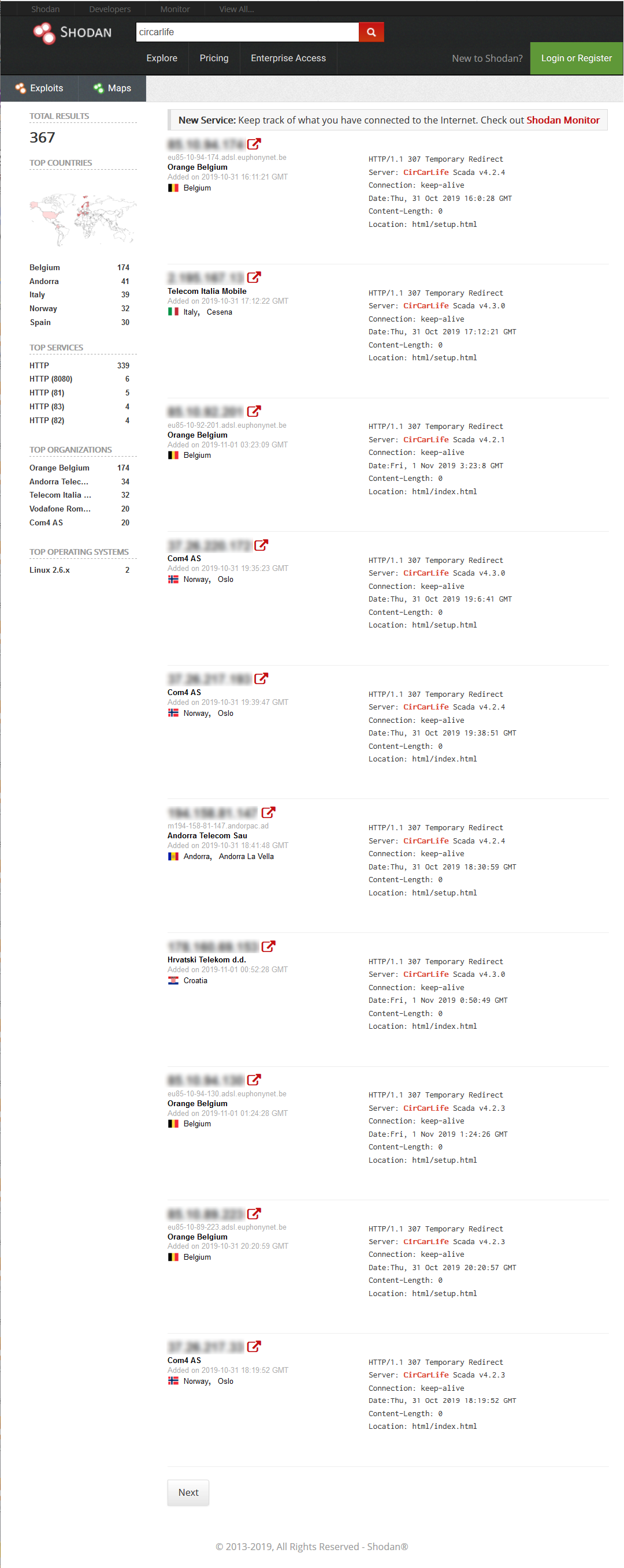
There are 367 CIRCONTROL devices connected to Internet. Those devices are across Belgium, Italy, Norway, Croatia, Andorra, etc. Some of the IP shown by Shodan are protected by password. But some are vulnerable and everyone can reach them via Internet.
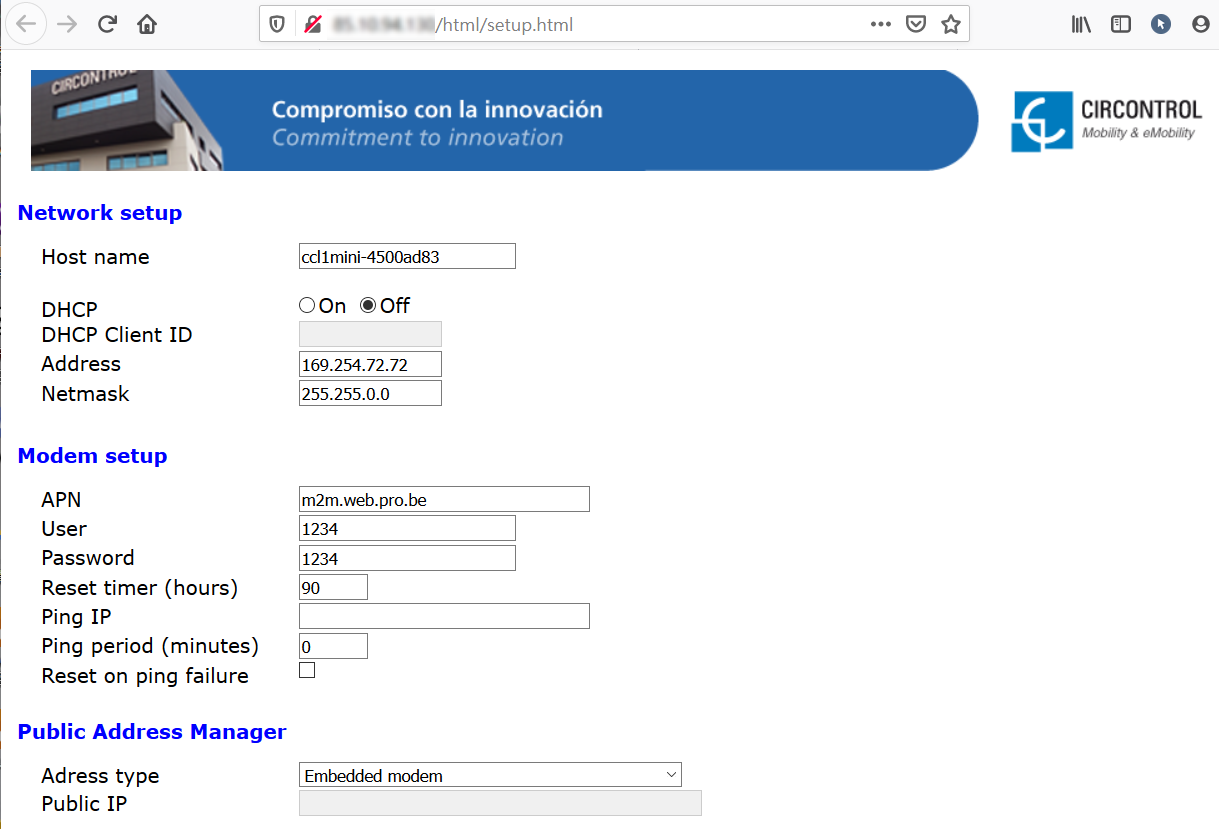
As you can see, anyone can modify those fields easily. For example, the password can be changed and only resetting that device can restore to the default password.
We hope CIRCONTROL takes the responsibility to upgrade all the firmware of the vulnerable devices before the disaster arrives.
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.

