Hsinchu, Taiwan – May 25, 2021 – The Darkside cyber-criminal gang attacked Colonial Pipeline, the largest pipeline system for refined oil products in the United States, with its targeted ransomware in May 7, 2021. The company asked the help of FireEye security company to investigate. The ransomware uses Salsa20 and RSA-1024 encryption algorithms and it means the possibility of decrypting those encrypted files without private key is really tiny.
The Colonial Pipeline shut down its 5,550-mile gasoline pipeline soon. This leads to panic buying of gasoline in the Southeast of US. The US government relaxed rules on fuel being transported by road to minimize disruption to supply. Also, President Biden signed an Executive Order to improve the nation’s cybersecurity and protect federal government networks and FBI began investigating this ransomware case. FBI confirmed that the Darkside is responsible for the Colonial Pipeline catastrophe.

The Darkside received the ransom, 5 million $USD, from The Colonial Pipeline. However, the Colonial Pipeline found the speed of using the Darkside decryption tools and private key to restore the files is too slow. They decide to use the backup data finally. It shows that backing up files frequently is always the reliable method against ransomware.
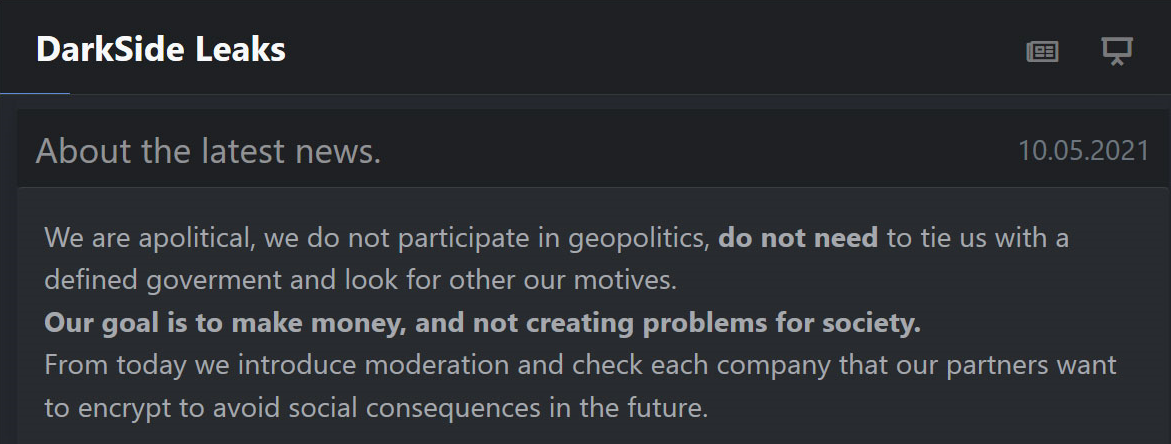
Meanwhile, the Darkside announced that their “goal is to make money, and not creating problem for society”. In May 15, 2021, they lost access to their infrastructure, including their blog, payment, and CDN servers. Therefore, the Darkside shuts down. It is interesting that the attacker this time is probably the REvil gang, another cyber-criminal group. The REvil representative said its program was introducing new restrictions - it would be forbidden to attack those institutions in healthcare, educational and government sector of any country.
The vulnerabilities used by Darkside ransomware are CVE-2020-17132 and CVE-2021-26855. Both of them are Microsoft Exchange Server RCE Vulnerability. The Darkside sends a lot of spam mails with attachments which will trigger these vulnerabilities. Some employee may click the attachments and ransomware begins spreading and destroying.
Lionic already studied these CVE and have designed virus signature in local and cloud signature. Any products which adopted Lionic’s Anti-Virus technology can protect against the Darkside ransomware.
- Partial Anti-Virus local signature examples about blocking Darkside ransomware
| VID | Virus Signature Name | Signature version |
|---|---|---|
| 7018380 | Trojan.Win32.Darkside.trNG | 3.0.1556 |
| 7018382 | Trojan.Win32.Darkside.trNI | 3.0.1557 |
| 7018383 | Trojan.Win32.Darkside.trNJ | 3.0.1557 |
| 7018384 | Trojan.Win32.Darkside.trNK | 3.0.1557 |
| 7018385 | Trojan.Win32.Darkside.trNL | 3.0.1557 |
- Partial Anti-Virus cloud signature examples about blocking Darkside ransomware
| VID | Virus Signature Name | Adding Date |
|---|---|---|
| 9273845030476747 | Trojan.Win32.Darkside.j | 2021-05-12 |
| 9212223015230098 | Trojan.Win32.Darkside.j | 2021-05-13 |
| 9227620288687023 | Trojan.Win32.Darkside.j | 2021-05-14 |
| 9154241571155251 | Trojan.Win32.Darkside.j | 2021-05-14 |
| 9226656176227054 | Trojan.Win32.Darkside.j | 2021-05-14 |
The Pico-UTM 100, the security network bridge made by Lionic, has these anti-virus signatures, of course. There are many other ransomwares targeted the enterprises. So far Lionic has collected more than 30 million of ransomware instances. Although local signature can only choose thousands of the high priority ones, the Lionic cloud-based anti-virus database has them all. If those big companies can deploy large volume of Pico-UTM 100 in their LAN in advance, we think their impact will be minimized, or even no impact.
References:
- Defense One, https://twitter.com/DefenseOne
- “Colonial Pipeline paid close to $5 million in ransomware blackmail payment”, https://www.zdnet.com/article/colonial-pipeline-paid-close-to-5-million-in-ransomware-blackmail-payment/
- “Colonial Pipeline attack: Everything you need to know”, https://www.zdnet.com/article/colonial-pipeline-ransomware-attack-everything-you-need-to-know/
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.

