Hsinchu, Taiwan – Jul 08, 2021 – The REvil is a group of cyber-criminals who used ransomware to attack companies and earn ransom. Also, they may steal important data of companies and try to sell or threaten to open. It is difficult to pinpoint their exact location, but they are thought to be based in Russia due to the fact that the group does not target Russian organizations, or those in former Soviet-bloc countries. They made many ransomware events in 2020, 2021. For example, REvil group stole plans for upcoming Apple products from Quanta Computer which is said to include plans for a pair of Apple laptops, a new Apple Watch and a new Lenovo ThinkPad in Apr, 2021.
The Kaseya is a software company which provides IT (Information Technology) management software for MSP (managed service provider) and IT teams. For those companies which do not have enough IT guys, the VSA (Virtual System Administrator) product of Kaseya provides service and software to help the monitoring and management of that company.
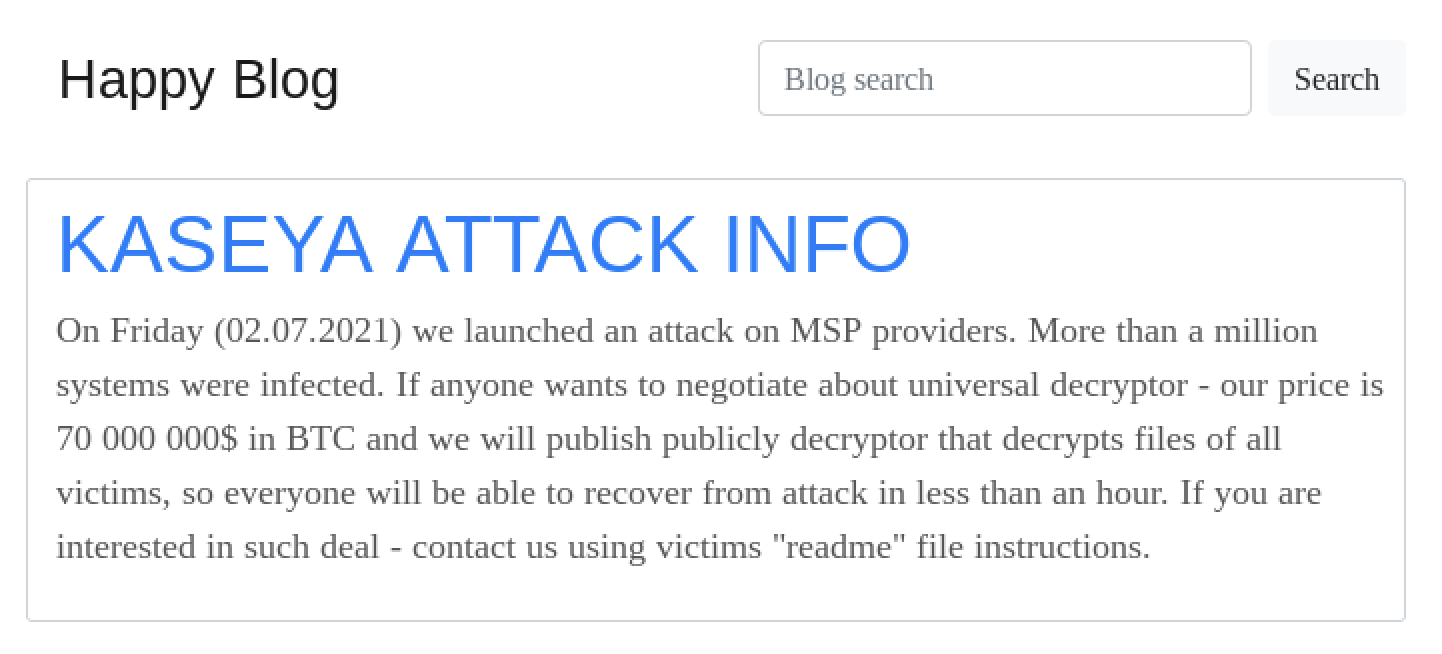
Security researcher found that there are some zero-day exploits in Kaseya VSA product. While Kaseya has made security patches and is validating them, the REvil gang attack Kaseya based on the zero-day exploit successfully. Unfortunately, the security patch is not provided in time. It is estimated about 1,500 downstream victims because their networks managed by MSPs using Kaseya remote management tools. After attacking successfully, REvil threatened to publish the information of victims on their page ‘Happy Blog’ unless the ransom is received. And REvil gang is demanding $70 million to unlock computers swept up in this widespread ransomware attack.
The REvil operators use some existing vulnerabilities and exploited some zero-day vulnerabilities in Kaseya VSA. According to TrueSec report, The high-level steps of the exploit are as follows -
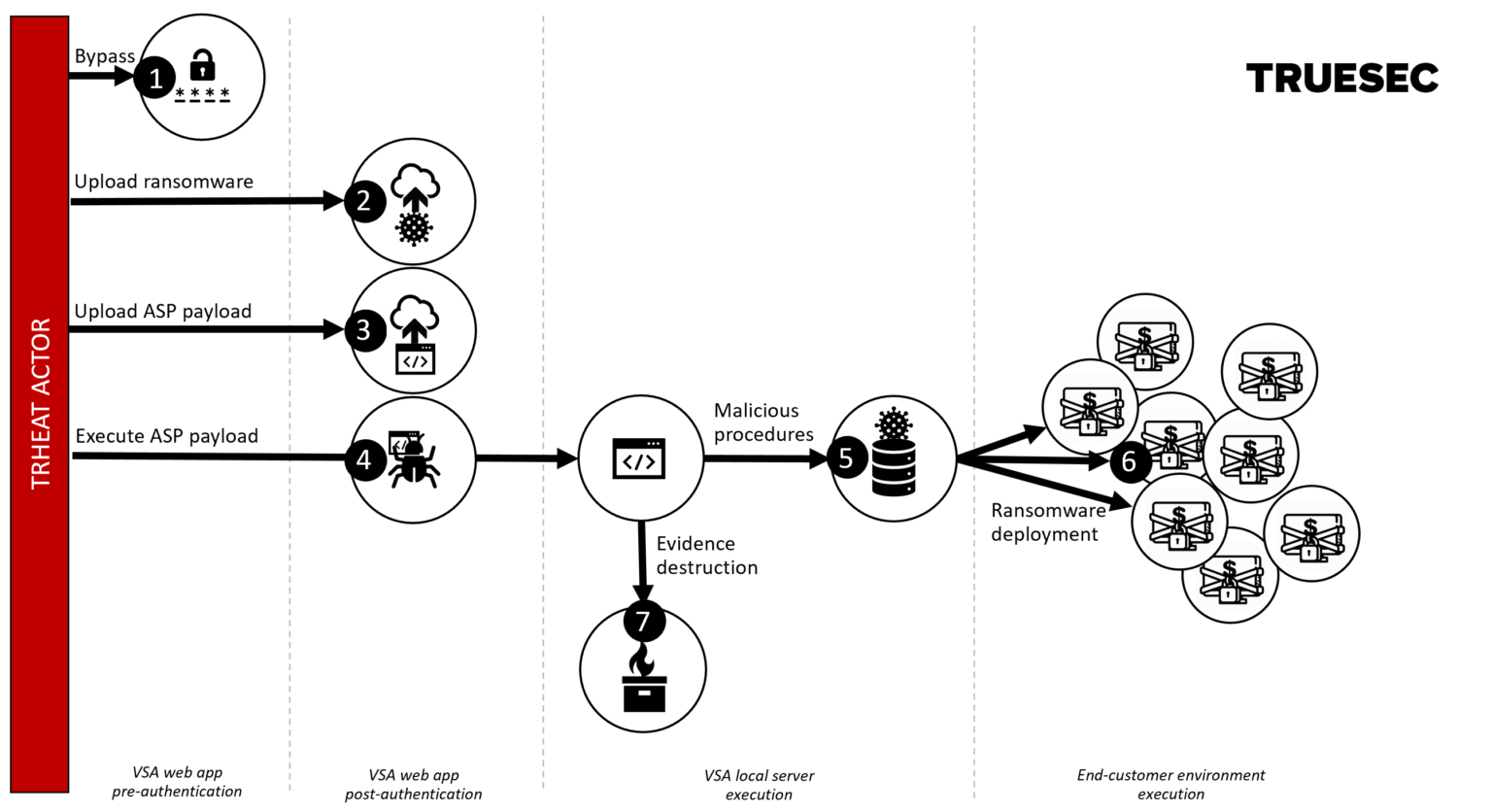
- Obtained an authenticated session by abusing a flaw in the authentication logic CWE-304 in /dl.asp.
- Uploaded the revil ransomware (agent.crt) through an unrestricted upload vulnerability CWE-434 while also bypassing the request forgery protection CWE-352 in /cgi-bin/KUpload.dll.
- Uploaded the ASP payload (screenshot.jpg) in the same fashion as described in 2.
- Invoked the payload in screenshot.jpg through a local code injection vulnerability CWE-94 in userFilterTableRpt.asp.
- Created Kaseya procedures to copy file and execute the ransomware.
- Executed the procedures.
- Removed logs and other forensic evidence.
After Lionic collect and study more information of this REvil ransomware, two Anti-Intrusion rules are designed to protect against this Kaseya VSA ransomware -
- rule sid 8100623: Blocking the authentication bypass attack, that is, the step 1 in above figure.
- rule sid 8100624: Blocking the uploading malicious script, that is, step 3 in above figure.
Also, the hash values of the collected REvil ransomware instances are added into the Lionic Cloud Anti-virus. If the user device adopted Lionic cloud anti-virus feature, the REvil ransomware in this event will be blocked. Therefore, both the anti-virus and anti-intrusion features of Lionic products can stop this REvil ransomware.
The Pico-UTM 100, the security network bridge made by Lionic, has these anti-virus signatures, of course. There are many other ransomwares targeted the enterprises. So far Lionic has collected more than 30 million of ransomware instances. Although local signature can only choose thousands of the high priority ones, the Lionic cloud-based anti-virus database has them all. If those big companies can deploy large volume of Pico-UTM 100 in their LAN in advance, we think their impact will be minimized, or even no impact.
References:
- REvil - Wikipedia, https://en.wikipedia.org/wiki/REvil
- “Kaseya: Roughly 1,500 businesses hit by REvil ransomware attack”, https://www.bleepingcomputer.com/news/security/kaseya-roughly-1-500-businesses-hit-by-revil-ransomware-attack/
- “Kaseya VSA - Unified Remote Monitoring & Management”, https://www.kaseya.com/products/vsa/
- “CVE-2021-30116: Multiple Zero-Day Vulnerabilities in Kaseya VSA Exploited to Distribute REvil Ransomware”, https://zh-tw.tenable.com/blog/cve-2021-30116-multiple-zero-day-vulnerabilities-in-kaseya-vsa-exploited-to-distribute-ransomware
- “How the Kaseya VSA Zero Day Exploit Worked”, https://blog.truesec.com/2021/07/06/kaseya-vsa-zero-day-exploit/
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.

