Updated on Febuary 22, 2022 - Added Asustor DeadBolt news.
Hsinchu, Taiwan – Feb 16, 2022 – NAS (Network Attached Storage) becomes an important device for many companies nowadays. Its first role is like common repository. The employee can have their PC mount file systems on NAS and access the NAS files just like the local files.
For the conveniences of customers, most NAS vendors keep porting popular open source projects as software packages and are running the package marketplace. Customers are easy to find suitable packages and install them into NAS for extending the functionalities of NAS. So NAS can play more and more roles after software packages are installed.
In addition to the storage role, NAS can be a small router (if NAT (network address translator) and routing packages installed.), a web server (if web server package installed) or a CMS, Content Management System, (if web server and CMS packages installed). Many SOHO and small business can buy one NAS for storage and also run its own website. This is the typical example of the Internet-connected NAS.
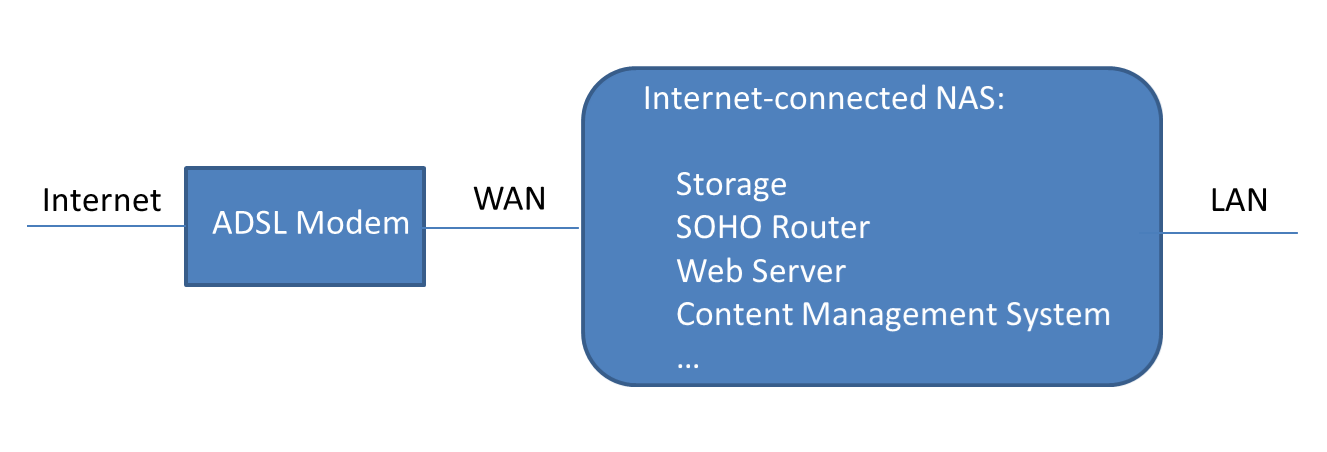
The traditional ransomware does not aware NAS. It is executed accidentally on an employee’s PC and then tries to encrypt all files of certain types (for example, doc, ppt and pdf file types) on that PC. If that PC has mounted NAS, the all accessible files of the same types on the NAS are encrypted, too.
However, more and more ransomware is developed to target some popular NAS (Network Attached Storage) devices recently. That means ransomware will be executed on NAS and encrypt files on NAS directly. The following are the example news -
“Qlocker ransomware returns to target QNAP NAS devices worldwide”, published on January 15, 2022.
“QNAP: DeadBolt ransomware exploits a bug patched in December”, published on January 31, 2022.
“eCh0raix Ransomware Variant Targets QNAP, Synology NAS Devices”, published on August 10, 2021.
“If You Own an Asustor NAS, Shut It Down Now”, published on Febuary 22, 2022.
| Ransomware | Target | Related Vulnerability | Date of Discovery | Fixed by NAS Vendor |
|---|---|---|---|---|
| Traditional Ransomware |
All NAS | Infected PC will write to NAS | N/A | N/A |
| QLocker | Qnap | CVE-2021-28799 | 2021 Apr | Yes |
| QLocker2 | Qnap | CVE-2021-28799 | 2022 Jan | Yes |
| DeadBolt | Asustor, Qnap | QSA-21-57 | 2021 Dec | Yes |
| eCh0raix | Qnap, Synology | CVE-2021-28799 | 2020 Sep (The Dual Targeting One) |
Yes |
Lionic collects ransomware speedily
Lionic has many sources to collect malware. One of the important sources is VirusTotal, a Google company, which provides a file scanning service. Users can upload a suspicious file, and then the suspicious file will be scanned by more than 50 anti-virus scanners simultaneously from its security partners. Lionic, one of the VirusTotal partners, has contributed one anti-virus scanner and thus have the permission to download malware samples for research purpose. These malware includes ransomware, of course.
By the accumulation of all the malware sources, Lionic can collect popular malware in a very fast way. So far, Lionic has collected several millions of ransomware.
Detecting all the several millions of ransomware can be done via the Lionic Anti-virus Cloud Service. All Lionic security technology based products can protect against most ransomware if its Lionic Anti-virus Cloud feature is enabled. Lionic Pico-UTM can block these several millions of ransomware by the Lionic Anti-virus Cloud feature, too.
Partial list of QLocker, QLocker2, DeadBolt and eCh0raix anti-virus rules -
| Rule ID | Virus Name | Release Date |
|---|---|---|
| 9180725719208975 | Trojan.HTML.Generic.4 | 2022-02-12 |
| 9043640864308621 | Trojan.HTML.Generic.4 | 2022-02-01 |
| 9054210322802889 | Trojan.UKP.Linux.4 | 2022-01-30 |
| 9171958368206968 | Trojan.Linux.DeadBolt.j | 2022-01-29 |
| 9056676768323737 | Trojan.Linux.DeadBolt.j | 2022-01-29 |
| 9009533873290614 | Trojan.Win32.Cryptor.j | 2022-02-06 |
| 9202786042402221 | Trojan.Win32.Cryptor.j | 2022-01-27 |
| 9234975713784048 | Trojan.Win32.Cryptor.j | 2022-01-18 |
| 9019819288383361 | Trojan.Win32.Cryptor.j | 2022-01-10 |
| 9225453927744141 | Trojan.Win32.Cryptor.j | 2022-01-07 |
| 9220929347718330 | Trojan.Win32.Cryptor.j | 2022-01-04 |
| 9244773324073811 | Trojan.Win32.Cryptor.j | 2022-01-04 |
| 9009590191037680 | Trojan.Win32.Cryptor.j | 2022-01-03 |
| 9001447397952038 | Trojan.Win32.Cryptor.j | 2021-11-29 |
| 9007545832202094 | Trojan.Win32.Cryptor.j | 2021-11-28 |
| … | … | … |
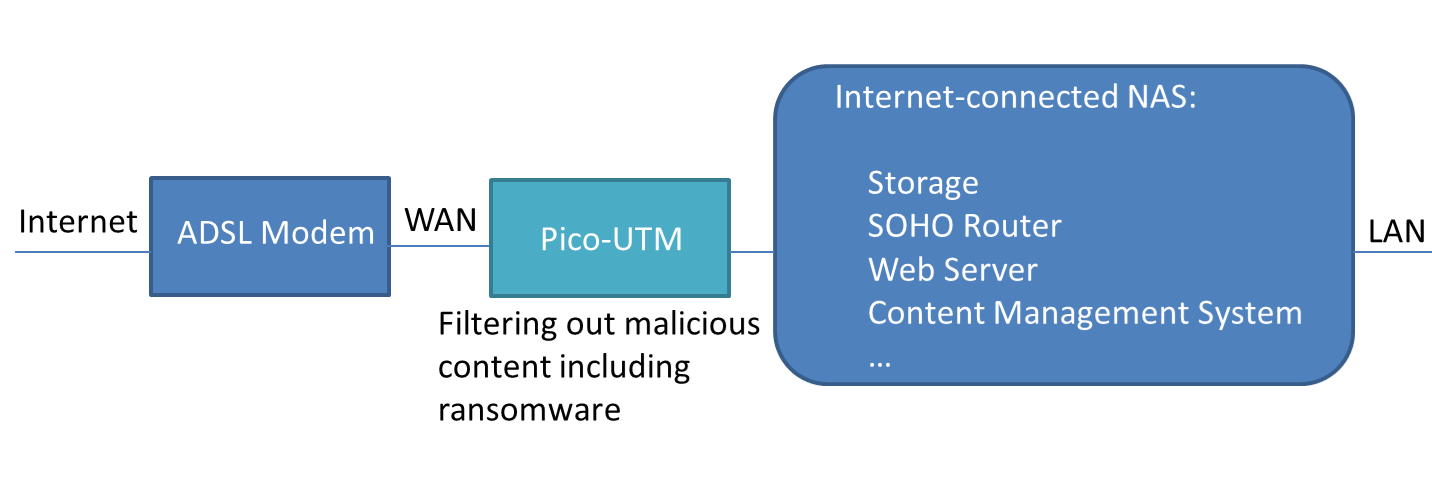
Pico-UTM can protect Internet-connected NAS
Since NAS is usually busily used in modern business, many newly manufactured NAS are designed with faster network interface like 2.5 Gigabit Ethernet or 10 Gigabit Ethernet. Pico-UTM may not be suitable for this high bandwidth situation so far.
However, there are some NAS connected to Internet directly. Pico-UTM is suitable for protecting these Internet-connected NAS. It is because WAN speeds are usually lower than the speed of Pico-UTM.
Conclusion
Many NAS packages are ported from open source projects. Although stable versions of open source projects are used for porting to packages, there are still some vulnerabilities are found suddenly. And then the developers of open source projects will fix it urgently. Sometimes urgent works bring more bugs. If you are a Internet-connected NAS owner, can you imagine that a vulnerability is found among your used packages, but the fixed package is not ready yet? Cyber-criminals may have done the ransomware which uses this vulnerability and begin trying all the accessible NAS on Internet.
In this situation, we strongly recommended to adopt Lionic Pico-UTM as the “Virtual Bug Fix”. It can filter out malicious content including ransomware, network intrusions and others. Internet-connected NAS owner can wait for vendor’s patch in a peaceful mood.
References:
- “Qlocker ransomware returns to target QNAP NAS devices worldwide”, https://www.bleepingcomputer.com/news/security/qlocker-ransomware-returns-to-target-qnap-nas-devices-worldwide/
- “QNAP: DeadBolt ransomware exploits a bug patched in December”, https://www.bleepingcomputer.com/news/security/qnap-deadbolt-ransomware-exploits-a-bug-patched-in-december/
- “eCh0raix Ransomware Variant Targets QNAP, Synology NAS Devices”, https://threatpost.com/ech0raix-ransomware-variant-qnap-synology-nas-devices/168516/
- “If You Own an Asustor NAS, Shut It Down Now”, https://www.tomshardware.com/news/if-you-own-an-asustor-nas-shut-it-down-now
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.