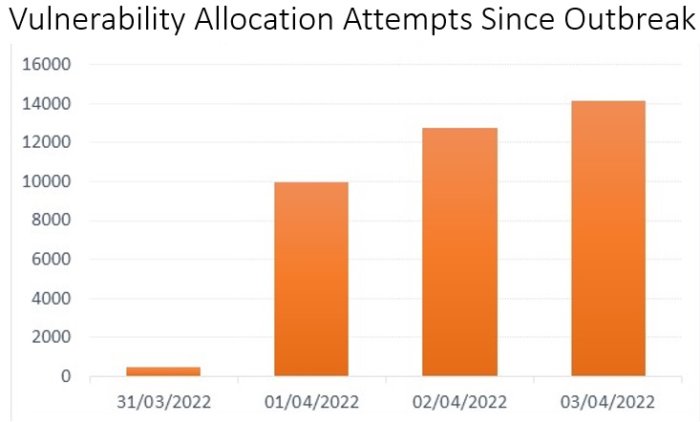
Hsinchu, Taiwan – Apr 28, 2022 – The Spring4Shell zero-day vulnerability is dropped on Mar 29, 2022. It is assigned as CVE-2022-22965. The CVE-2022-22965 is in the popular Java Spring framework and allowed remote code execution (RCE). The exploit attempts targeting the critical Spring4Shell (aka SpringShell) across cloud services are found after two days.
The score of CVE-2022-22965 is 9.8 and it means CRITICAL. If your Internet-connected servers adopted Tomcat, Java and Spring Framework, they may be attempted to exploit or attacked already.
| CVE Id | CVE Description | CVSS v3 Score | Severity Level | Affected Software |
|---|---|---|---|---|
| CVE-2022-22965 | A Spring MVC or Spring WebFlux application running on JDK 9+ may be vulnerable to remote code execution (RCE) via data binding. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e. the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it. | 9.8 | Critical | Several software configurations of JDK and Spring Framework are affected. Please check here for detail. |
Anyway, Java Spring Framework should be updated to the latest version which is version 5.3.19 at the time of writing.
Spring4Shell and CVE-2022-22965
Spring Framework running on JDK version 9 and newer are vulnerable to a Remote Code Execution (RCE) attack due to a bypass for CVE-2010-1622. Because there is a public proof-of-concept available, many people are able to download it and try to exploit some servers.
To exploit this vulnerability, what an attacker needs to do is sending crafted HTTP requests to the vulnerable system. The widely spreading proof-of-concept program of CVE-2022-22965 contains the following payload.
class.module.classLoader.resources.context.parent.pipeline.first.pattern=
class.module.classLoader.resources.context.parent.pipeline.first.suffix=
class.module.classLoader.resources.context.parent.pipeline.first.directory=
class.module.classLoader.resources.context.parent.pipeline.first.prefix=
class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=
While using this proof-of-concept, attackers can upload arbitrary files (e.g., a backdoor or a web shell) to the server. Then, they can get full control of the server by accessing these web shell.
Partial list of Anti-Intrusion rules for CVE-2022-22965
As usual, Lionic Security Team analyzed this CVE-2022-22965 immediately and released the anti-intrusion rules for defending against Spring4shell vulnerability on Apr 1, 2022. All Lionic security technology based products can block CVE-2022-22965 after this releasing.
| Rule ID | Description |
|---|---|
| 8101179 ~ 8101182 | Apache Tomcat Java ClassLoader Access attempt |
| … | … |
Conclusion
Plenty of companies runs Java Spring Framework based web services. Therefore, many cyber-criminals adopted this zero-day vulnerability immediately and developed their own intrusion tools, botnet, worms or others. For example, the infecting part of new Mirai malware is using Spring4shell vulnerability instead. Since new version of Spring Framework is arrived, software upgrade is the the best method for pulling the plug.
However, if network administrators are tired of fixing the endless stream of cybersecurity vulnerabilities, they can use the Lionic Pico-UTM as the “Virtual Bug Fix”. Sometimes the first patch may not be good enough or found other new vulnerabilities. If the Pico-UTM is protecting the server, the network administrators can take their time to wait for the stable version and then upgrade.
References:
- “springcore-0day-en”, https://github.com/tweedge/springcore-0day-en
- “CVE-2022-22965”, https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-22965
- “CVE-2022-22965 Detail”, https://nvd.nist.gov/vuln/detail/CVE-2022-22965
- “Microsoft detects Spring4Shell attacks across its cloud services”, https://www.bleepingcomputer.com/news/security/microsoft-detects-spring4shell-attacks-across-its-cloud-services/
- “VMware patches Spring4Shell RCE flaw in multiple products”, https://www.bleepingcomputer.com/news/security/vmware-patches-spring4shell-rce-flaw-in-multiple-products/
- “Mirai malware now delivered using Spring4Shell exploits”, https://www.bleepingcomputer.com/news/security/mirai-malware-now-delivered-using-spring4shell-exploits/
- “16% of organizations worldwide impacted by Spring4Shell Zero-day vulnerability exploitation attempts since outbreak”, https://blog.checkpoint.com/2022/04/05/16-of-organizations-worldwide-impacted-by-spring4shell-zero-day-vulnerability-exploitation-attempts-since-outbreak/
About Lionic Corporation
Lionic Corporation is a worldwide provider of innovative Deep Packet Inspection solutions. The technologies of Lionic include the complete DPI-based software engine and related management software which offer the Security Solutions that addresses anti-virus, anti-intrusion, anti-webthreat; and the Content Management Solutions that addresses application identification, device identification, application based QoS, web content filtering, parental control.
Lionic’s security and content management solutions, cloud-based scan services and signature subscription service are widely deployed in the world already. They help service providers, network appliance manufacturers, semiconductor companies, etc. to enable the next generation of business routers, residential gateways, SD WAN edges and cloud gateways, advanced firewalls, UTMs, Smart NICs and mobile devices. Those products powered by Lionic provide better network management and protect the world’s networks from an ever increasing level of security threats.